VPNs don’t always mean fraud—but combined with other behaviors, they can raise red flags. Here’s how modern fintech risk engines handle VPN signals

Fraud Detection in Fintech: What VPN Usage Can Signal
A true blue millennial trying to engineer her full time-career around the world of content. How cliché is that?
Table of Contents

The rapid digitization of financial services has opened new frontiers for innovation—but it has also expanded the attack surface for fraud. As fintechs offer services like KYC, payments, account verification, and embedded banking, the stakes for fraud detection are higher than ever.
Among the many tools fraudsters use to conceal their identity and location, Virtual Private Networks (VPNs) stand out. But here’s the nuance: VPNs are not always malicious. Many privacy-conscious users, developers, and even remote teams use them legitimately. The challenge lies in contextually interpreting VPN signals to distinguish risk from routine.
Why VPNs Complicate Fintech Risk Models
A VPN masks a user’s real IP address and encrypts their internet connection. While this enhances user privacy, it can disrupt risk signals that fintech platforms typically rely on—like geolocation, device identifiers, and IP-based reputation scoring.
According to this information source, VPNs are now a common tool for users seeking a secure internet experience. In regions like India and Southeast Asia, VPN usage is growing rapidly due to increasing privacy awareness, tighter regulatory environments, and high mobile internet penetration.
In a fintech context, however, this increased VPN adoption introduces complexity. For example, a user initiating a high-value payment or accessing an account from an unfamiliar IP masked by a VPN could resemble a fraud attempt—even when it’s not.
Common Fintech Scenarios Where VPNs Impact Risk
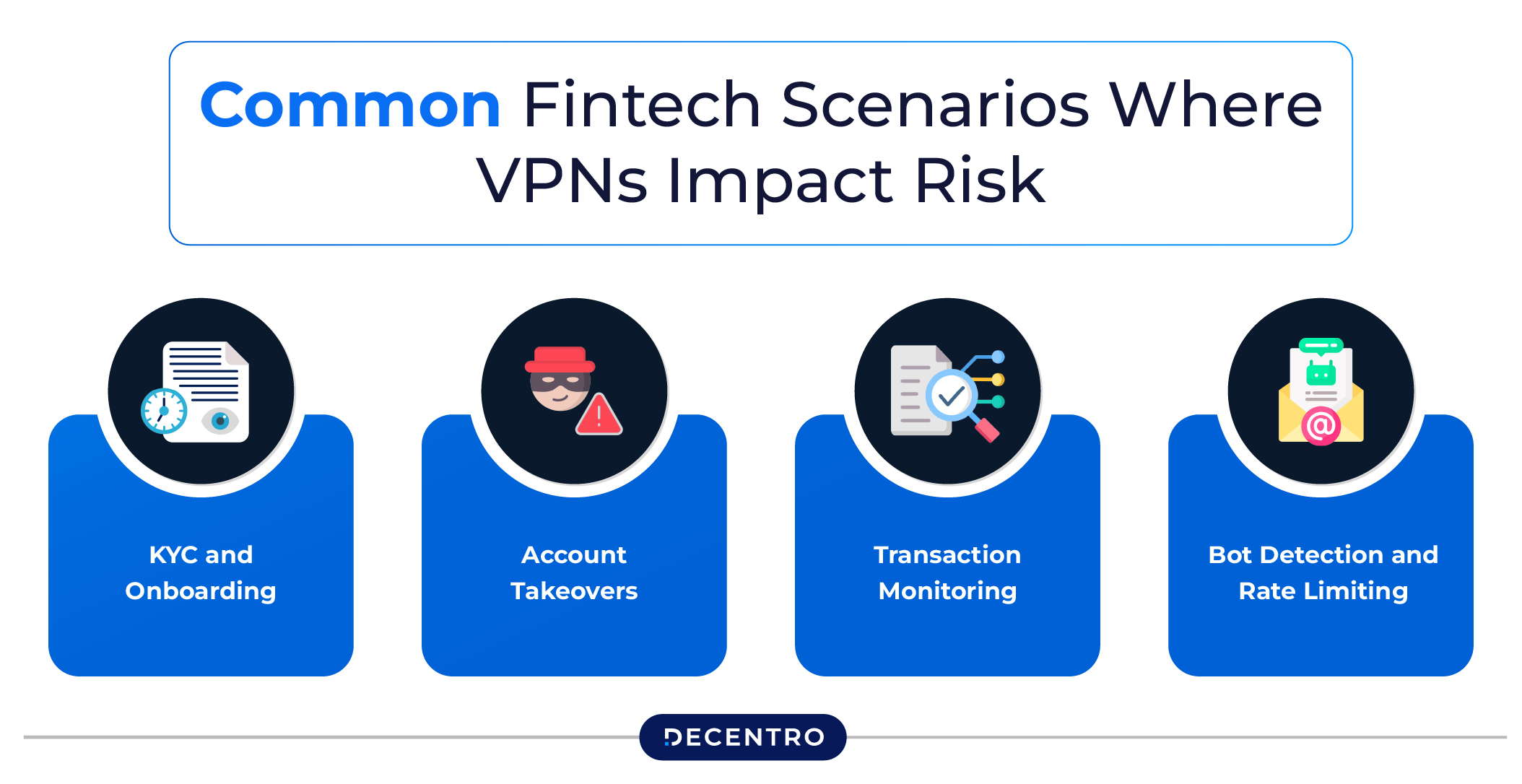
Understanding how VPN usage can interfere with fraud detection is key to building robust, context-aware systems. Here are a few examples:
- KYC and Onboarding: VPNs can obscure IP-based geo-verification, making it harder to match a user’s claimed identity with their actual location.
- Account Takeovers: Fraudsters using compromised credentials often use VPNs to hide their location, making it difficult to track suspicious logins.
- Transaction Monitoring: High-value transactions made via VPNs from unfamiliar devices may trigger fraud rules, requiring escalation or manual review.
- Bot Detection and Rate Limiting: VPNs can be used to cycle IPs, mimicking human activity across multiple accounts.
When VPN Use Signals Potential Fraud

VPN usage alone is not a reliable fraud marker, but it becomes significant when combined with additional data points:
- Device or Session Anomalies: A previously unseen device using a VPN to access a long-established account.
- Behavioral Mismatches: Sudden changes in spending, login times, or access patterns while on a VPN.
- Velocity Risks: Several accounts accessed from a single VPN endpoint within a short time span.
- Synthetic Identity Flags: VPNs paired with inconsistent KYC details or disposable email IDs can indicate synthetic profiles.
Building Context-Aware Fraud Detection Systems
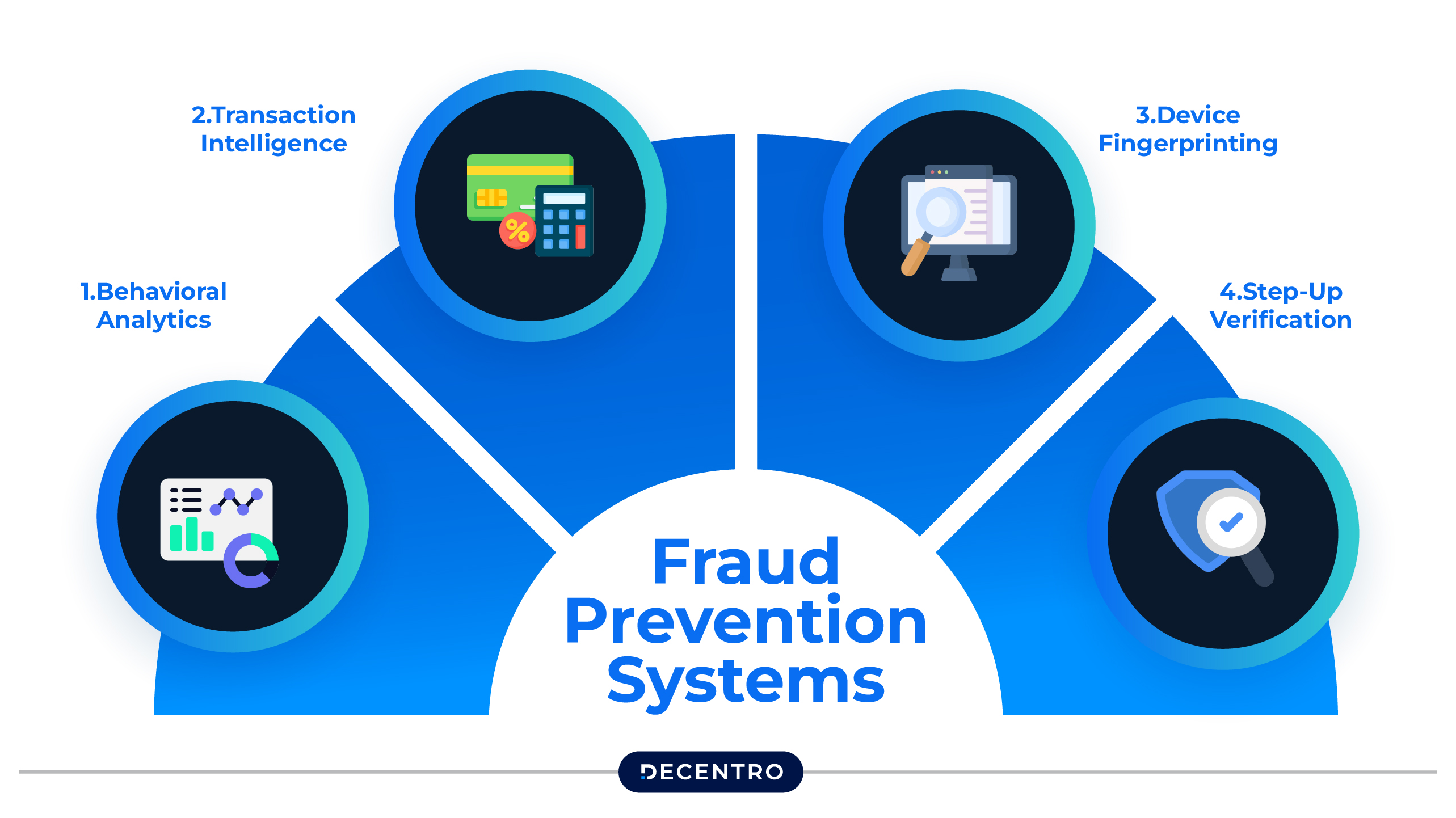
To deal with the nuances of VPN usage in fintech, organisations must adopt multi-layered fraud prevention systems that evaluate behaviour in context.
1. Behavioral Analytics
Track user patterns over time. Consistent VPN use from the same device and network can indicate legitimate use. Sudden, erratic activity could trigger further checks.
2. Transaction Intelligence
Combine VPN data with transaction patterns—amounts, frequency, and beneficiary details. A VPN alone may be harmless, but combined with rapid high-value transfers, it becomes a red flag.
3. Device Fingerprinting
Fingerprinting tools help tie sessions to specific devices even when IP addresses change. A known, trusted device using a VPN may still be low-risk.
4. Step-Up Verification
When multiple risk markers coincide—like VPN + new device + unusual activity—systems can trigger additional verification methods like OTP, biometric checks, or document verification.
VPNs and Emerging Threats in Fintech
As fraud tactics evolve, VPN usage is being combined with more sophisticated methods:
- Residential Proxies: Harder to detect than traditional VPNs, these mimic regular IP addresses.
- Mobile Device Emulators: Used to bypass device fingerprinting while routing traffic through VPNs.
- AI-Driven Fraud Bots: Combine VPN use with human-like behavior to bypass security layers.
To counter these tactics, fintechs must continually update their risk scoring algorithms with fresh threat intelligence and behavioral data.
Should Fintechs Block VPNs Altogether?
Blocking VPNs entirely is not advisable. Doing so can harm user experience, especially for:
- Individuals accessing fintech apps on public Wi-Fi networks.
- NRIs accessing domestic accounts from abroad.
- Users in regions with limited or censored internet access.
- Developers and QA engineers testing apps from different environments.
Instead of blanket bans, platforms should:
- Log and monitor VPN traffic.
- Assess in context rather than in isolation.
- Apply graduated responses (e.g., additional verification).
Best Practices for Managing VPN Use in Fraud Detection

1. Leverage Multi-Signal Risk Scoring
Incorporate VPN indicators into broader risk scoring models that also include location, device, transaction type, and behavior.
2. Maintain VPN Intelligence Feeds
Use databases of known VPN exit nodes, residential proxies, and TOR IPs. Flag traffic accordingly and assign weighted risk scores.
3. Build Adaptive KYC Flows
Design onboarding and verification processes that can adapt when VPN usage is detected—e.g., asking for alternate proof of location.
4. Educate Risk & Fraud Teams
Train internal teams to identify common fraud patterns involving VPNs and avoid false positives by over-indexing on privacy tools.
5. Communicate Transparently With Users
When additional checks are triggered due to VPN usage, explain the rationale clearly. Transparency builds trust and reduces churn.
Regulatory Compliance and VPN Data
India’s Digital Personal Data Protection (DPDP) Act and global regulations like GDPR place restrictions on how personal data can be collected and processed.
When handling VPN-related data:
- Ensure purpose limitation: Use VPN indicators only for fraud prevention.
- Avoid automatic rejection: Decisions based solely on VPN use may be considered discriminatory.
- Maintain audit trails: Justify actions taken due to VPN-based flags to comply with regulatory scrutiny.
The Future: VPN Usage as a Norm, Not an Exception
As consumer awareness of digital privacy grows, the use of VPNs will become more normalized. Fintech platforms should view this not as a threat, but as an evolving signal within a complex fraud landscape.
By investing in contextual analysis, adaptive authentication, and ongoing threat intelligence, companies can stay ahead of bad actors without compromising the experience of genuine users.
Final Thoughts
VPN usage is no longer niche—it’s a core part of how people engage with digital products today, including financial services. While it does introduce complications into fraud detection models, the key lies in understanding when and how VPNs matter.
Rather than blocking VPNs outright or assuming malicious intent, fintechs should incorporate them into broader fraud frameworks, combining behavioural analytics, device intelligence, and transaction context to make smarter, more user-friendly decisions.
Looking to integrate with an eligible banking and infrastructure partner? Drop in a hi at hello@decentro.tech and we will get in touch.


