A deep dive into the impact of payment frauds on businesses and consumers. Find out how to mitigate risks and protect yourself with Decentro’s KYC Banking APIs.

Payment Frauds: The Hidden Risks Behind Digital Transactions
A true blue millennial trying to engineer her full time-career around the world of content. How cliché is that?
Table of Contents

In the fiscal year 2023, the Reserve Bank of India (RBI) was confronted with a grave issue of payment fraud, surpassing a staggering 302.5 billion rupees.

This alarming figure, while a decrease from the 1.3 trillion rupees reported in 2021, still signifies a significant threat to India’s financial stability.
If we have to set the context for this exponential increase, it has to be attributed to the significant spike in the number of digital payments in India. Innovation in the payments landscape, regulatory support, the increase in smartphone penetration and cheaper mobile internet access have played a key role in adopting digital transactions and their rapid growth in India, furnishing some numbers such as
- The total volume of digital payment transactions increased from 2,071 crores in FY 2017-18 to 13,462 crores in FY 2022-23, at a CAGR of 45 per cent.
- The Unified Payments Interface (UPI), which crossed the 11 billion mark in October with 11.41 billion transactions and witnessed a downfall in November with a total of 11.24 billion transactions, has now scaled a new peak in December in terms of transaction volume and value.
Now that we have set the context of the sheer volume of money moved in our country, let’s decode how this volume comes with the risk of payment fraud and scams that people must be aware of.
The Payment Frauds Landscape
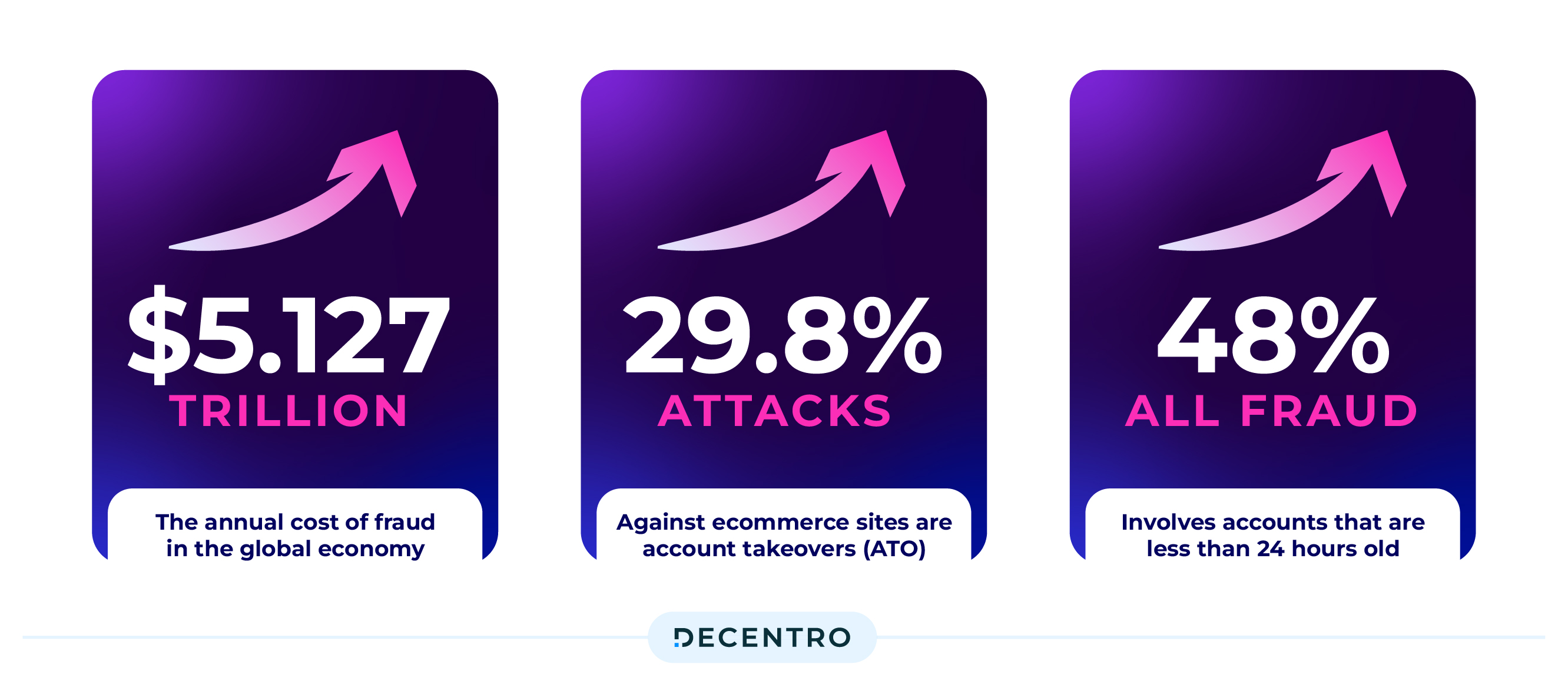
In India’s financial sector, 2023 has been marked by a surge in sophisticated scams that exploit evolving technologies and capitalise on unsuspecting individuals. The economic realm has witnessed various fraudulent activities, from the pervasive rise of UPI-related frauds to cunning schemes enticing victims with unrealistic investment returns. Payment frauds, including QR code scams, credit card frauds, part-time job deceptions, and the alarming emergence of courier scams targeting the youth, have added new dimensions to the threat landscape.
Payment fraud isn’t just bad news for individual consumers; it’s also a significant drain on businesses defrauded annually. By 2030, payment card fraud losses are projected to hit $49 billion and snowball yearly.
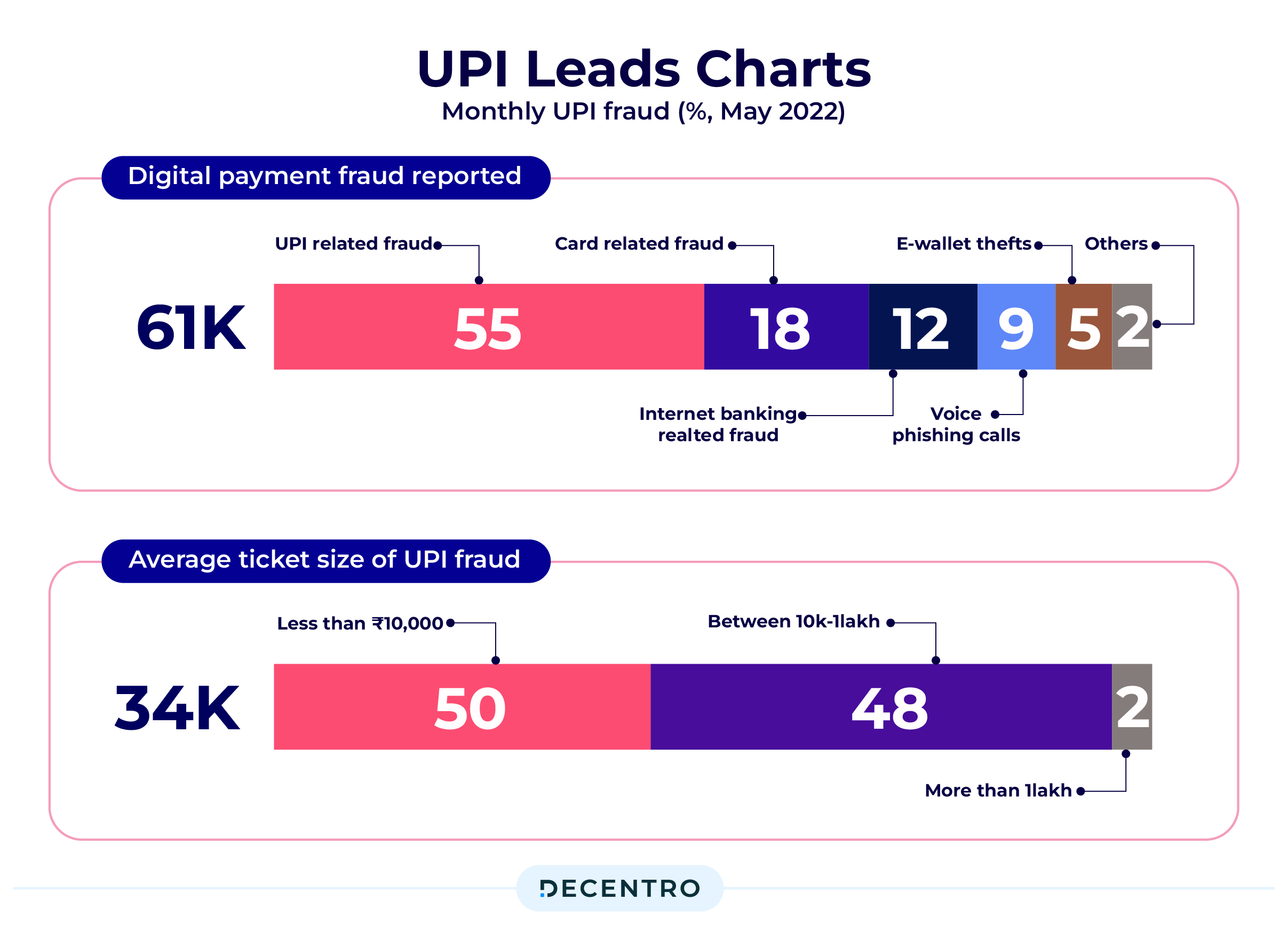
While 3,596 frauds, amounting to 155 crore using cards and internet banking services, were reported in FY22, the volume nearly doubled to 6,659 digital frauds in FY23, amounting to 276 crore. However, 94.5% of the frauds reported in FY23 by value occurred in previous financial years, and there were delays in identifying fraud and subsequent lag in reporting by lenders.
These numbers from various verified sources, while potentially excluding numerous undetected payment frauds, indicate the dire need to focus on combating these alarming numbers.
So, taking a step back,
What is a Payment Fraud?
Payment fraud is a type of financial fraud that occurs when someone intentionally uses false or stolen payment information to make a purchase. Fraudulent actors might use stolen credit card information, create fake cheques, or make unauthorised electronic fund transfers.
Retail businesses are particularly vulnerable to payment fraud because they handle many transactions and may not have the resources to vet each payment method thoroughly.
What are the Types of Payment Fraud?

Some common types of payment fraud include:
Friendly Fraud
Friendly Fraud happens when a customer purchases online with their credit card but then contacts the credit card issuer and initiates a chargeback.
In these situations, customers will contact the credit card issuer, claiming that the item wasn’t delivered or it was returned, but they didn’t receive a refund. In some cases, they might even claim that they don’t remember making a purchase and that their credit card has been compromised.
Triangulation
One of the most common types of payment fraud is called triangulation. The name of this method implies that there are three participants in the transaction: the unsuspecting customer, the online store, and the stolen data.
A triangulation fraud typically happens in the following way:
- A legitimate customer purchases a product from a third-party marketplace seller, who is also a fraudster.
- Then, the fraudster places the order on a genuine retailer (for example, Amazon or eBay) for the same product that the customer ordered.
- However, the illegitimate third-party seller (the fraudster) pays for the transaction with stolen payment information to complete the payment. It is usually a credit card that was purchased on the dark web.
- The genuine seller processes the order and sends the product to the customer’s shipping address, which he provided during checkout.
- The customer receives the ordered item, but the merchant (the authentic retailer) processes a fraudulent transaction.
This is risky among all types of payment fraud because the customer may never realise that something isn’t going as it should. Since they received the product they ordered, nothing seems out of the ordinary, and they might even leave a positive review for the fraudster, boosting his rankings.
Clean Fraud
Clean fraud refers to fraudulent transactions that appear legitimate, which can be a huge problem for merchants since the transaction is not permanently blocked or flagged up.
What’s distinctive about this payment fraud is that fraudsters use accurate data to commit their cybercrimes, impersonating the original cardholder.
While friendly fraud hides behind fake identities or stolen data, hackers who commit clean fraud usually have extensive knowledge of cardholders and their credit card details.
So, they use customer data to fool the systems into thinking that the hacker is the cardholder.
Phishing Attacks
A phishing attack is commonly called the practice of sending fraudulent communications to potential victims.
Their purpose is to trick the recipients into thinking the message comes from a reputable source and lure them into giving away their private information. Most commonly, fraudsters will ask for the user’s credit card and/or bank account details and other personal data such as name or address.
Some of the most common phishing scams include:
Email phishing
Statistics show that more than 96% of phishing attacks happen via email. This method typically involves “spray and pray,” in which fraudsters impersonate a legitimate organisation or identity and then send mass emails to as many addresses as possible.
Phishing emails often entail a threat or a sense of urgency, informing the recipient that they must make an urgent payment or their account has been compromised. The purpose is to encourage them to take action as soon as possible.
Once the victim clicks on the malicious link and fills out the data requested, the fraudster has access to the information.
Spear phishing
As opposed to email phishing, this one of the types of payment fraud uses the “spray and pray” method to send mass emails to thousands of recipients; spear phishing takes on a more personalised approach. This means that hackers will send malicious emails to specific individuals within a company.
These emails are built in a more personalised way to convince the victim that they are a legitimate individual or organisation.
Whaling
This method of payment fraud is very similar to phishing. However, instead of targeting regular employees within an organisation, hackers target high-level executives such as the CEO, CTO, CFO or individuals in senior positions. In other words, what we would consider “the big fish” in slang—hence the term whaling.
Again, these emails transmit urgency, making individuals feel compelled to act immediately.
Smishing
Among the popular types of payment fraud is smishing, a phishing attack that uses text messages instead of email communication.
However, it works on the same principle, sending mass text messages that appear to be sent from a reliable source or a trusted organisation. Instead, they contain malicious links to steal people’s personal and payment data.
Vishing
Another alternative to phishing is vishing, which uses phone calls to execute the fraud. This method is usually disguised as an automated voice message from a legitimate organisation claiming that you have a debt you must immediately pay.
For example, they may say that your insurance has expired or that suspicious activity on your bank account needs to be handled immediately. The ultimate goal is to obtain the victim’s payment information.
Wire Transfer Scams
A wire transfer scam, or wire fraud, occurs when a fraudster poses as a trusted source (e.g., a vendor, family member, or company) and requests an immediate wire transfer of funds to their account. Scammers usually try to create a sense of urgency or manipulate victims.
Merchant Identity Fraud
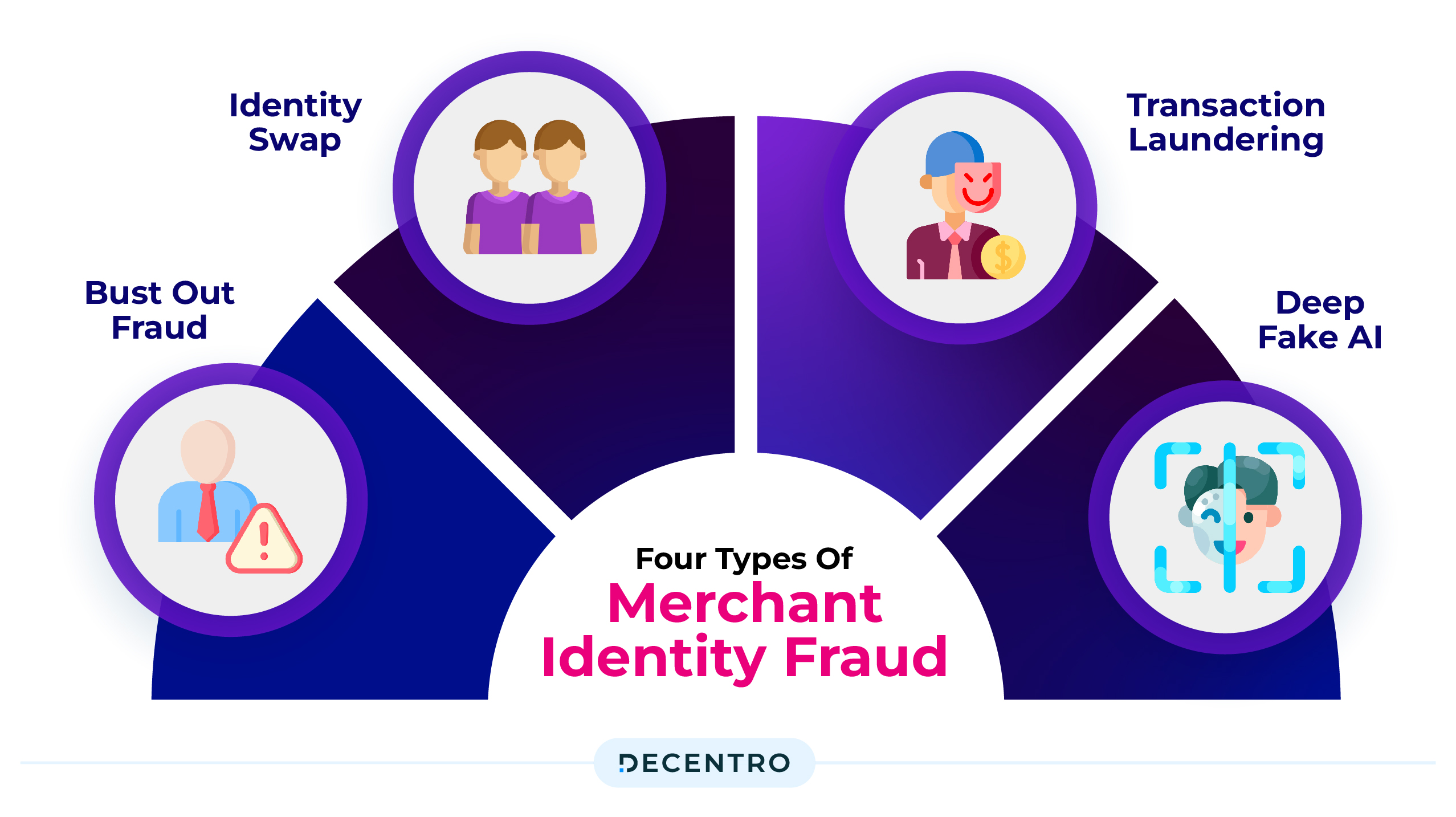
One of the types of payment fraud that affects merchants the most is merchant identity fraud. It involves scammers setting up a merchant account, presenting themselves as a legitimate business, and then charging stolen credit or debit cards.
There are four types of merchant identity fraud:
• Bust Out Fraud – In this scheme, a merchant sets up a merchant account without intending to operate as a legitimate business. This account is then used to process fraudulent transactions.
• Identity Swap – Identity swap refers to cases where a merchant uses a fake or stolen identity to secure a merchant account. This often happens when the fraudster is prohibited from opening an account independently.
• Transaction Laundering – Transaction laundering happens when an unknown company uses the payment credentials of an approved merchant to process payments that the acquirer is unaware of.
• Deep Fake AI – Deep fake AI refers to artificial intelligence (AI) technology designed to create deep phoney content. Deep fake AI algorithms can analyse and manipulate existing media to generate highly realistic phoney content that convincingly depicts individuals saying or doing things that never occurred. While deep fake AI has legitimate uses in entertainment and digital media production, it poses significant risks, especially when spreading misinformation, identity theft, fraud, and privacy violations, and, in this case, even unauthorised transaction laundering.
Common Payment Channels that are prone to Frauds
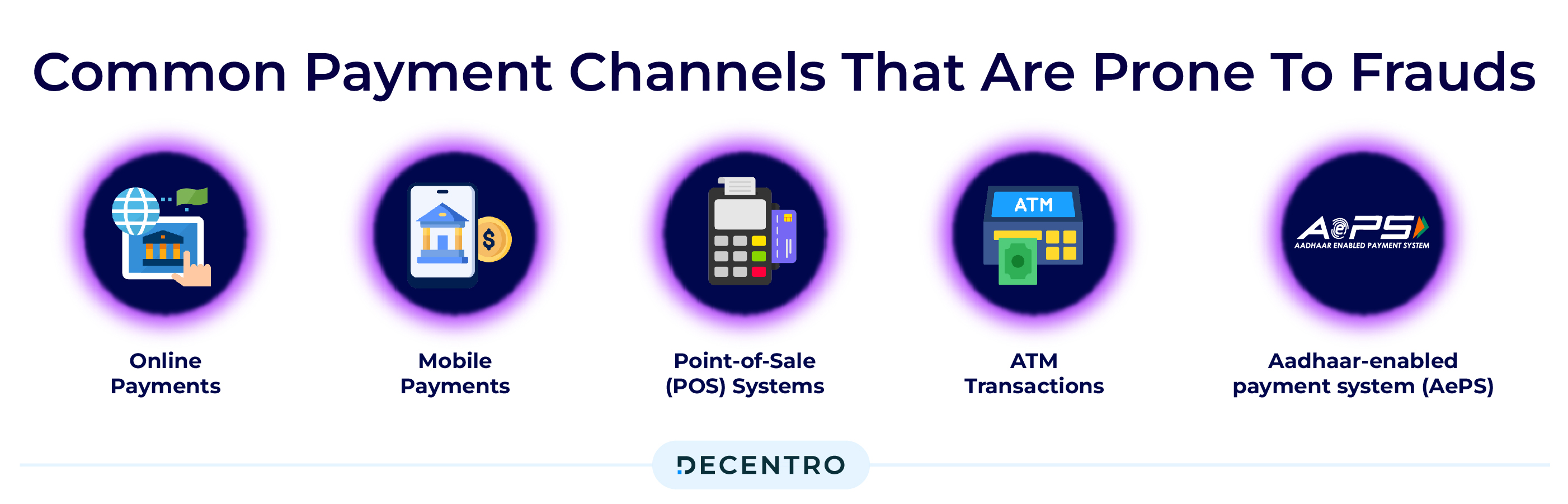
Payment fraud can occur across various payment channels, but fraudsters more commonly target some channels due to their vulnerabilities or widespread usage. Here are some of the top payment channels that are often infiltrated by payment fraud:
- Online Payments: Online payment channels, including e-commerce websites, mobile apps, and online platforms, are prime targets for payment fraud due to the anonymity and ease of transactions. Fraudsters exploit vulnerabilities such as stolen credit card information, phishing attacks, and account takeovers to make unauthorised purchases or transactions.
- Mobile Payments: With the increasing popularity of mobile payment apps and digital wallets, mobile payment channels have become lucrative targets for fraudsters. Fraudulent activities include account takeover attacks, SIM swapping, and unauthorised transactions from compromised devices or accounts.
- Point-of-Sale (POS) Systems: Payment terminals used in retail stores, restaurants, and other businesses are vulnerable to payment card skimming, where fraudsters install illegal devices to capture credit or debit card information during transactions. Additionally, POS systems can be targeted by malware or hacking attacks, compromising transactions and stealing payment data.
- ATM Transactions: Automated teller machines (ATMs) are frequently targeted by fraudsters using card skimming devices or ATM malware to steal cardholder information and personal identification numbers (PINs). This information is then used to create counterfeit cards or make unauthorised withdrawals.
- Aadhaar-enabled payment system (AePS): AePS is a payment service that allows a bank customer to use Aadhaar as his/her identity to access his/ her Aadhaar-enabled bank account and perform basic banking transactions such as balance inquiries, cash deposits, cash withdrawals, and remittances through a Business Correspondent/Agent.
- In 2023, Aadhar Enabled Payment System (AePS) frauds were 11% of the cyber financial scams with origins in India, according to an analysis by the Indian Cyber Crime Coordination Centre (I4C). Most of these were committed in Bihar and Jharkhand.
Impact of Payment Fraud

As per a report by a leading cybersecurity firm, India witnessed a 65% increase in payment fraud cases in 2023, with financial losses exceeding INR 1200 crore. UPI frauds constituted around 40% of these incidents, reflecting the vulnerabilities in even the most popular digital payment methods.
- Impact on Businesses: The direct impact on businesses includes financial losses, operational disruptions, and costs associated with investigating fraud and strengthening security measures. For example, a survey of Indian SMEs revealed that approximately 30% had experienced financial losses due to payment fraud, impacting their annual revenue by an average of 5%.
- Effect on Consumer Trust: Payment fraud indirectly severely affects consumer trust and confidence in digital transactions. A study indicated that 60% of consumers in India are hesitant to engage in online transactions following reports of high-profile fraud cases. This hesitancy can reduce customer engagement and loyalty, impacting long-term business growth.
Regulatory Framework in India

India’s regulatory framework has been formulated to safeguard the interests of both businesses and consumers against identity theft and payment fraud
RBI Guidelines and IT Act Provisions
- RBI Guidelines: The Reserve Bank of India (RBI) issues periodic guidelines to regulate digital payments. Essential guidelines include mandatory two-factor authentication for online transactions, KYC (Know Your Customer) norms for payment services, and directives for immediately reporting fraudulent transactions.
- IT Act Provisions: The Information Technology (IT) Act, especially the cybersecurity and data protection sections, plays a crucial role in digital payments. For example, Section 43A mandates reasonable security practices for handling sensitive personal data, and Section 72A stipulates penalties for breach of privacy.
Regulations Specific to Online Transactions and Data Security
- Data Localisation Requirements: RBI mandates that all payment system operators store data related to payment systems in India. This includes full end-to-end transaction details and information collected/carried/processed as part of the message/payment instruction.
- Payment Security Standards: Compliance with international standards like PCI DSS (Payment Card Industry Data Security Standard) for merchants and payment gateways to ensure secure card transactions.
- Guidelines on Digital Payment Security Controls: Released in 2021, these guidelines cover various aspects of digital payment security and risk management, including mobile applications and Internet banking security.
Mitigating Payment Frauds
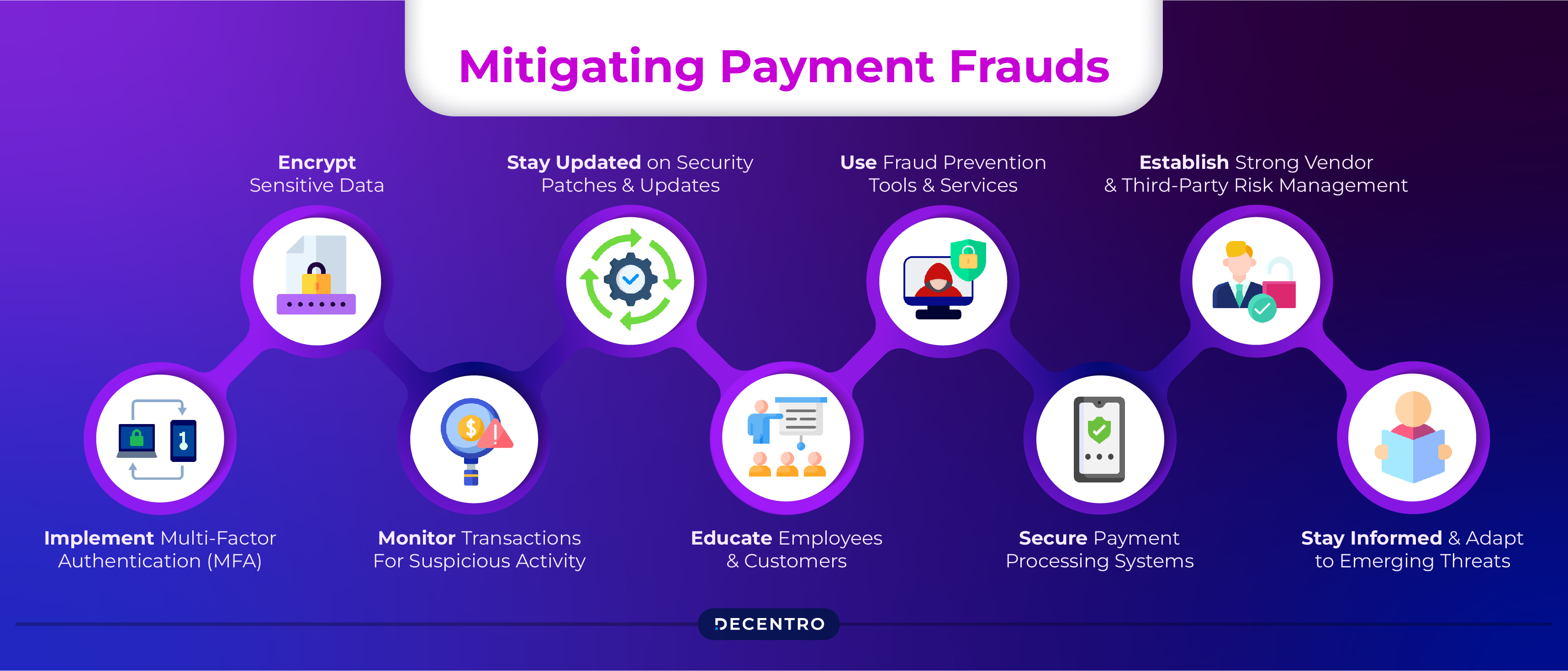
Mitigating payment fraud requires a proactive approach and a combination of strategies to protect against various fraudulent activities. Here are some practical measures to reduce payment fraud:
- Implement Multi-Factor Authentication (MFA): Require users to provide multiple verification forms, such as passwords, biometrics, or one-time codes sent via SMS or email, to access accounts or authorise transactions. MFA adds an extra layer of security and makes it harder for fraudsters to gain unauthorised access.
- Encrypt Sensitive Data: Utilize robust encryption methods to protect sensitive payment data, including credit card numbers, bank account details, and personal information, both in transit and at rest. Encryption helps prevent unauthorised access and reduces the risk of data breaches.
- Monitor Transactions for Suspicious Activity: Implement real-time monitoring systems and fraud detection tools to identify and flag suspicious transactions or patterns indicative of fraud. Automated monitoring can help detect anomalies, such as substantial transactions, multiple failed login attempts, or irregular purchasing behaviour.
- Stay Updated on Security Patches and Updates: Regularly update and patch payment processing systems, software, and applications to address known vulnerabilities and security flaws. Keep abreast of security advisories and software updates vendors release to protect against emerging threats.
- Educate Employees and Customers: Provide comprehensive training to employees and customers on security best practices, including how to recognise phishing attempts, avoid sharing sensitive information, and verify the legitimacy of transactions. Educated users are more likely to detect and prevent fraudulent activities.
- Use Fraud Prevention Tools and Services: Invest in advanced fraud prevention solutions, such as fraud detection algorithms, machine learning models, and behavioural analytics, to identify and prevent fraudulent transactions in real-time. These tools can help detect fraud patterns and anomalies that may go unnoticed by traditional methods.
- Secure Payment Processing Systems: Implement strong access controls, firewalls, and intrusion detection systems to protect payment processing systems and networks from unauthorised access and cyber-attacks. Restrict access to sensitive data and regularly audit system configurations for security compliance.
- Establish Strong Vendor and Third-Party Risk Management: Vet and monitor third-party service providers, payment processors, and vendors to ensure they adhere to stringent security standards and compliance requirements. Establish contractual agreements that outline security expectations and responsibilities.
- Stay Informed and Adapt to Emerging Threats: Stay abreast of the latest fraud trends, techniques, and attack vectors through industry reports, threat intelligence feeds, and information-sharing networks. Stay vigilant and adapt your fraud prevention strategies to address evolving threats effectively.
Future Trends and Predictions: Shaping the Landscape
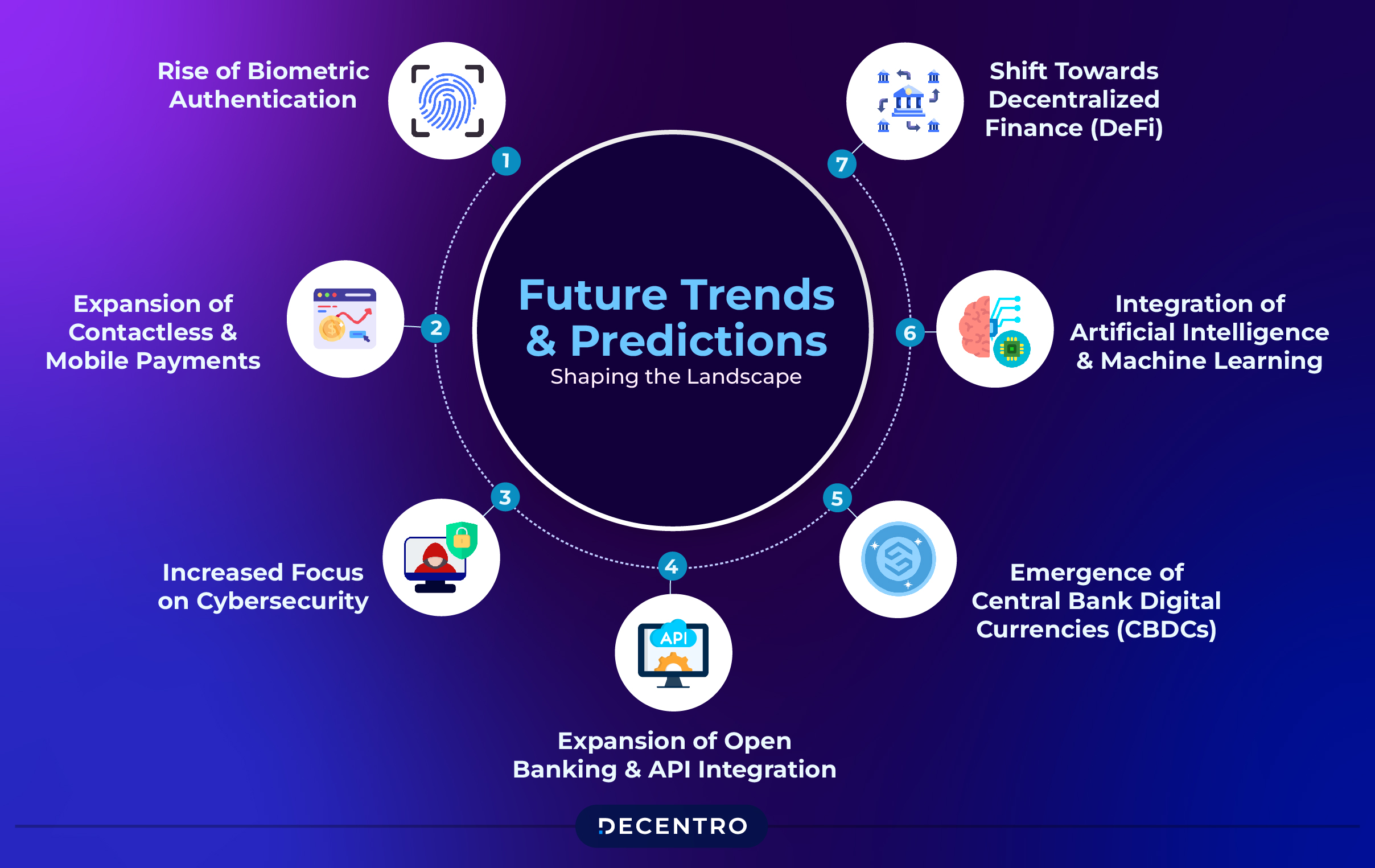
Navigating the complexities of payment fraud in the digital era is crucial for merchants to ensure the safety and trust of their transactions. Staying informed about the latest fraud trends, regularly updating security measures, and educating employees and customers are critical to mitigating these risks. Apart from these, we also have the following methods to reduce these risks.
- Rise of Biometric Authentication: Biometric authentication methods such as facial recognition, fingerprint scanning, and voice recognition are gaining popularity for enhancing security and convenience. As technology improves and biometric sensors become more widespread, we expect to see increased adoption of biometric authentication across various industries and applications, including payments and financial services, to combat identity theft-related frauds.
- Expansion of Contactless and Mobile Payments: The COVID-19 pandemic has accelerated the adoption of contactless and mobile payment methods as consumers seek safer and more hygienic ways to transact. This trend is expected to continue as consumers become accustomed to the convenience of tap-and-go payments and mobile wallet apps. Merchants and financial institutions must invest in infrastructure and technology to support the growing demand for contactless and mobile payments.
- Increased Focus on Cybersecurity: With the growing frequency and sophistication of cyber attacks, cybersecurity will remain a top priority for organisations across all sectors. We expect increased investment in cybersecurity technologies and practices, including threat intelligence, behavioural analytics, and endpoint security solutions. Additionally, regulatory bodies may introduce stricter cybersecurity requirements to protect consumer data and mitigate cyber risks.
- Expansion of Open Banking and API Integration: Open banking initiatives and adoption of application programming interfaces (APIs) are transforming the financial services landscape by enabling seamless and secure payments, data sharing and integration between banks, fintech companies, and third-party service providers. This trend will continue, driving innovation, competition, and collaboration within the financial ecosystem. As more banks and financial institutions embrace open banking principles, consumers can expect to benefit from a broader range of products and services tailored to their needs.
- Emergence of Central Bank Digital Currencies (CBDCs): Several central banks worldwide, including India, are exploring issuing digital currencies to complement physical cash. CBDCs can improve payment efficiency, financial inclusion, and effectiveness of monetary policy. While the adoption of CBDCs is still in its early stages, we expect to see continued experimentation and pilot projects in the coming years, with some countries potentially launching CBDCs for public use.
- Integration of Artificial Intelligence and Machine Learning: Artificial intelligence (AI) and machine learning (ML) technologies are increasingly integrated into payment systems and fraud detection solutions to enhance efficiency and accuracy. AI-powered algorithms can analyse vast amounts of transaction data in real-time to detect anomalies and identify fraudulent activity related to payments and identity theft more effectively than traditional methods. As AI and ML capabilities advance, we expect further innovation in fraud prevention, customer personalisation, and risk management.
- Shift Towards Decentralized Finance (DeFi): Decentralized finance (DeFi) platforms, which use blockchain technology to enable peer-to-peer financial services without intermediaries, are gaining traction as an alternative to traditional banking and economic systems. DeFi offers opportunities for greater financial inclusion, accessibility, and transparency but also presents security, regulation, and scalability challenges. As DeFi continues to evolve, we expect regulatory frameworks to adapt to accommodate these new financial models and technologies.
How Decentro Helps Businesses Reduce Fraud and Mitigate Risk
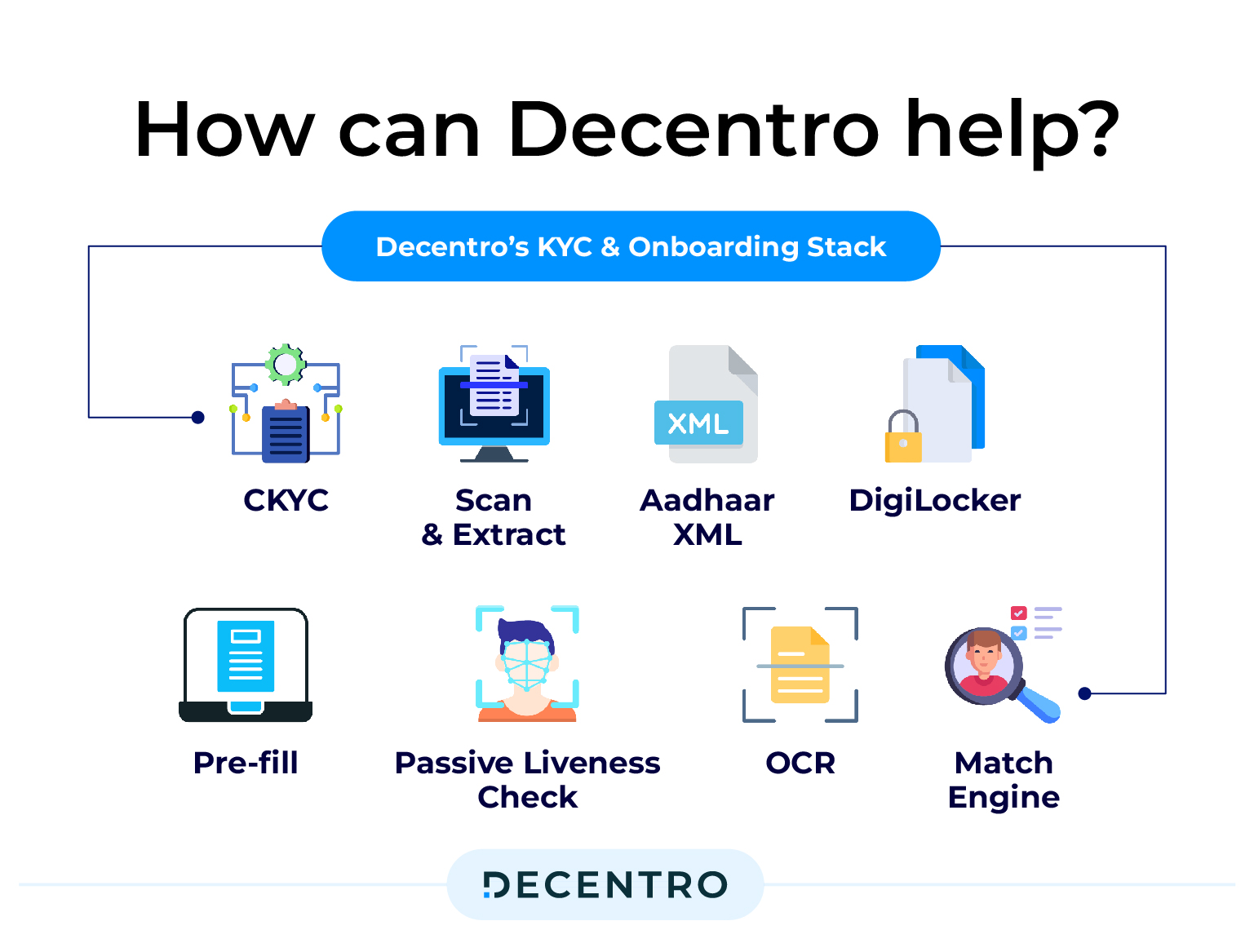
From a business perspective, when choosing a technology partner that can assist you with instant background verification and secure payments, there are several factors to consider, from the accuracy of the technology at hand to the customisation of the journey to best suit your needs.
This is where the KYC and onboarding suite of Decentro comes into play. With these APIs, you can establish the following:
Verification of Ownership
The background verification at the time of onboarding a new vendor/merchant/customer/user.
Validation of Existence
The need to validate the transactions before:
- Accepting funds from the users. This strengthens risk monitoring and ensures funds are flowing from the user’s registered bank account only
- Withdrawal/payout is made to the UPI ID of the user
With 800+ ID validations per hour and 500+ OCR and extractions per hour, Decentro fully understands the importance of a compliant and verified workflow.
We also have a cluster of other products, including APIs, SDKs, and Hyperstreams, that come under Decentro Farsight and are built to enable verification and validation and ensure your payment journey is secure and compliant. With advanced image recognition and machine learning capabilities, this Farsight offering enables precise document forensics, classification, extraction, masking, and fuzzy matching.
Maximum scrutiny, with minimum hassle.
Do you wish to integrate this into your product flow?


