Discover how AI agents for financial services improve customer experience, boost efficiency, and ensure compliance across banking and fintech.

AI Agents in Financial Services: The Complete Guide
Avi is a full-stack marketer on a mission to transform the Indian fintech landscape.
Table of Contents

It’s 11:55 PM on the last day of your billing cycle. A customer spots a strange ₹1,999 debit.
Before panic sets in, an AI agent has already flagged the anomaly, paused the card, checked recent UPI handles against a known-risk list, drafted a dispute, and opened a case—then messaged the customer on WhatsApp with the case ID and next steps. No hold music. No, “our lines are busy.” Just a calm, complete resolution.
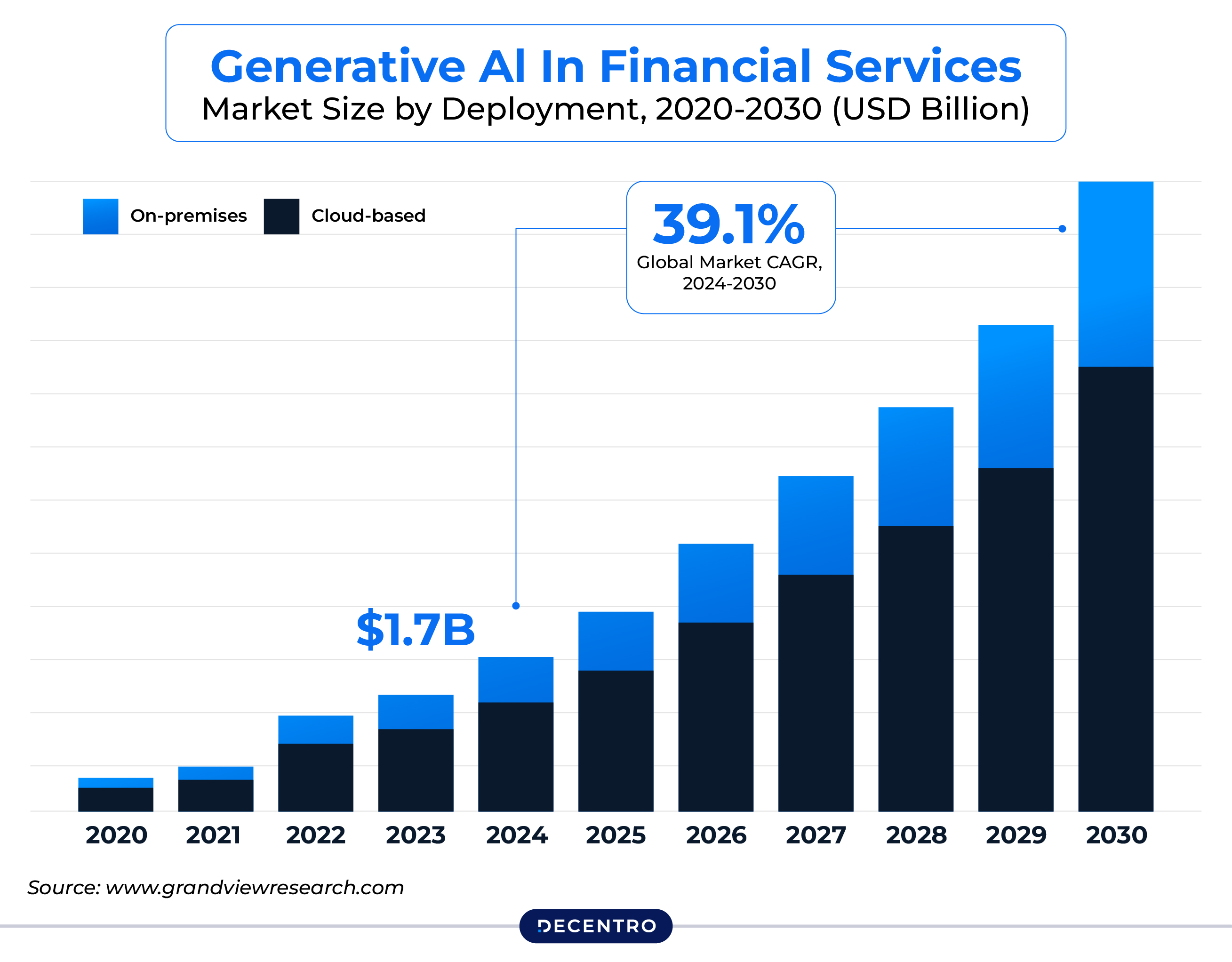
That’s the promise of AI agents in financial services. Not another chatbot that parrots FAQs, but agentic AI systems that can reason, take actions across tools, and close loops—safely, compliantly, and at scale. According to Markets and Markets, the global AI in finance market is projected to grow from $38.36 billion in 2024 to an impressive $190.33 billion by 2030.
This guide is a practical playbook for anyone interested in agents for Financial Services, across banks, NBFCs, fintechs, and wealth platforms, looking to move beyond pilots and turn agents into a durable, competitive advantage.
What Are AI Agents in Financial Services?
AI agents are software entities that combine language understanding with tool use (via APIs), contextual memory, and goal-driven planning to complete tasks with minimal human input. In financial services, they interface with core systems (CBS, LOS/LMS, payment rails), verification stacks (KYC/KYB), risk engines, and CRMs to decide, act, and verify results.
How do AI agents in financial services differ from other types of AI?
Unlike chatbots/LLMs (answer generators), ML models (predictors), or RPA (scripted click-replayers), AI agents are goal-seeking doers. They plan → act → verify, keep working memory, and call tools/APIs—CBS, LOS/LMS, KYC/KYB, payments, CRMs—to complete tasks end-to-end rather than just returning a response or a score.
In BFS, this means agents orchestrate the whole flow (e.g., fetch data via AA, run risk rules, create cases, update systems, trigger compliant comms), recover from failures with retries/fallbacks, and enforce guardrails and approvals with full audit trails. The result: measurable outcomes like shorter cycle times and reduced TAT, not just higher CSAT or model accuracy.
How they differ from legacy chatbots
| Topic | AI Agents (Financial Services) | Legacy Chatbots (Traditional Automation) |
| Goal | Execute outcomes end-to-end (plan → act → verify) | Answer FAQs, collect info, then hand off |
| Workflow | Multi-step orchestration across systems | Scripted, menu/intent trees |
| Tool/API use | Calls enterprise APIs (CBS, LOS/LMS, KYC/KYB, payments, CRM) | Little to no tool use; may raise a ticket |
| Memory & context | Working memory across steps/sessions | Shallow, session-bound context |
| Decisioning | LLM reasoning + rules/ML + policy guardrails | Rule-based intents; simple NLU |
| Error handling | Retries, fallbacks, re-plans, escalates | Breaks/loops on change; hands off to human |
| Compliance & audit | Pre-checks, approvals, explainable actions, full logs | Basic content filters; chat logs only |
| Security & deploy | Runs in VPC/edge; scoped credentials & RBAC | Usually a SaaS widget; limited data access |
| Metrics that matter | Cycle time/TAT ↓, success rate ↑, exceptions, SLA adherence | CSAT, deflection/containment, handle time |
| Change tolerance | Adapts to API/policy changes via config | Brittle to UI/flow changes |
| Typical use cases | Limit increase, collections workflow, dispute ops, onboarding | FAQ, password reset, appointment/lead capture |
TAT = Turnaround Time.
Autonomous vs. Reactive Systems
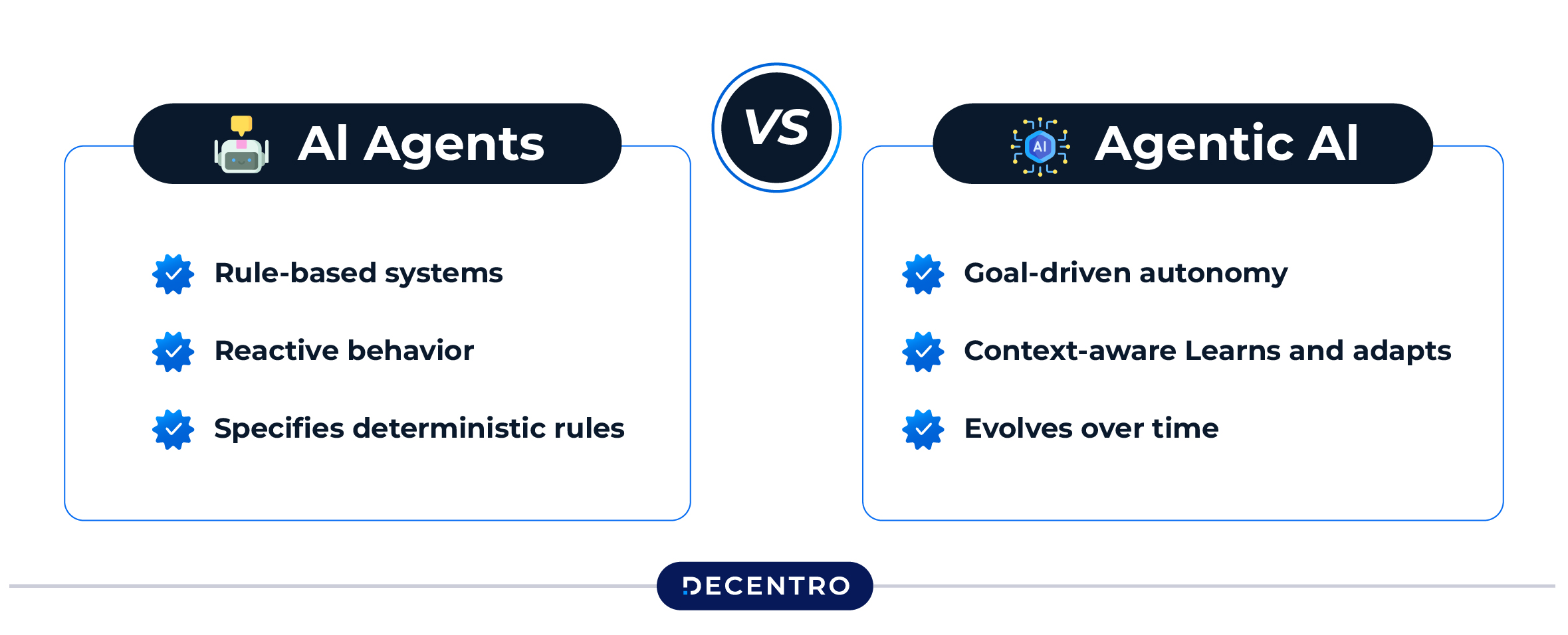
- Reactive agents respond to inbound messages (“What’s my EMI due date?”), Execute a few safe actions and report back.
- Autonomous agents work proactively, scanning ledgers for mismatches, monitoring fraud signals in real-time, or running daily “health checks” on mandates—raising tickets only when something requires a human touch. Most institutions start with a reactive approach and then graduate to autonomy with guardrails.
Multi-step workflow capabilities
Agents thrive on multi-hop tasks. But firstly, what are multi-hop tasks. Multi-hop tasks are jobs that take several linked steps to finish, where the output of one step becomes the input for the next, often across different tools or systems.
Examples (finance):
- Credit limit increase: fetch statements → run risk rules → update CBS → notify customer.
- KYB onboarding: verify PAN/Udyam → match directors → create account → trigger mandate.
Think of it like a relay race: each step passes the baton to the next until the goal is done.
Coming back, AI Agents thrive and excel especially on multi-hop tasks:
- Understand the goal (“update my communication address and re-send statement”).
- Break it down (verify identity → fetch address proof → update CRM → trigger email resend).
- Call the right tools (e.g., verification API, CRM API, email service).
- Check outcomes and close the loop with the customer.
Evolution: chatbots → assistants → agents
- Chatbots: scripted, FAQ-driven.
- Assistants: better understanding, limited actions.
- Agents: plan, act, verify, and learn.
In short: AI agents in finance are operators, not answer machines.
Core Capabilities & Use Cases
A) Customer Service Automation
Agents take an issue from “hello” to “resolved.” They detect intent, extract context from CRM/core systems, plan the steps, and execute actions (e.g., updating tickets, issuing refunds, running KYC checks) with approvals as needed. Every step is logged with a human-readable rationale, unresolved edge cases escalate to a human, and overall TAT drops with more consistent outcomes.
Where it shines
- Account inquiries: balances, statements, limits, KYC status, transaction categorisation.
- Loan servicing: EMI schedules, foreclosure quotes, NOC issuance, and address updates.
- Mandates & payments: set up UPI Autopay, eNACH status checks, mandate re-presentment.
- Fraud alerts: block cards, pause VPA, raise disputes, educate customers with next steps.
Micro-example
A borrower requests a foreclosure letter. The agent verifies identity via OTP + doc match, calculates outstanding (pulling from the ledger), generates the letter, and sends it by email—while logging the entire audit trail.
B) Risk Management & Compliance
Continuous control without extra headcount: Agents monitor transactions and risk signals 24/7, running policy checks before actions execute (e.g., limits, KYC/sanctions/PEP, consent). They auto-remediate small breaches (block, re-verify, re-route) and escalate edge cases for approval. Every step is time-stamped and auditable, thereby strengthening control without requiring additional personnel.
- Real-time monitoring: anomaly detection on incoming payments, payout velocity checks, and merchant risk scoring.
- Regulatory reporting support: prepare data slices for compliance teams, validate field completeness, and flag gaps for manual review.
- KYC/KYB hygiene: periodic refreshes, CKYC pulls, DigiLocker doc fetches, AML screening, and sanctions list monitoring (as per your policies/tools).
- Policy enforcement: agents can fork to “safe fallbacks” when a policy is triggered (e.g., additional verification for high-risk profiles).
C) Investment & Wealth Management
Personalised at the edge: Agents run on-device or inside your VPC, pulling portfolio and risk context to craft real-time recommendations and micro-actions (e.g., rebalance, pause SIPs, tax-loss harvest) with consent. Running near the data keeps latency low and privacy intact, while policy checks, approval thresholds, and complete audit logs are enforced automatically.
- Portfolio rebalancing suggestions based on risk tolerance, age, and cash-flow needs.
- Tax-aware actions such as harvesting gains/losses with client consent.
- Event-driven nudges: SIP date reminders, goal shortfall alerts, re-projection after life events (marriage, child, relocation).
Micro-example
The agent spots a large idle balance in a customer’s account while their SIPs are paused. It runs a quick scenario, proposes a phased re-entry plan, and schedules a human advisor callback for concurrence.
D) Credit Assessment & Fraud Detection
Speed with prudence: Agents pull multi-source data (bureau, bank, device, ID) in one pass, run fraud/risk rules and ML, and produce explainable decisions. Low-risk cases auto-approve with limits; edge/risky cases get step-up checks or human review. Result: sharply lower TAT without loosening controls, sanctions/KYC, velocity, and anomaly guardrails stay enforced end-to-end.
- Autonomous underwriting support: collect docs, verify income surrogates, pull bureau data, calculate DTI and scorecards, produce a recommendation/decline with a rationale for underwriter review.
- Behavioural analysis: repayment patterns, device intelligence, geo-velocity, merchant cluster risk.
- Fraud deflection: prompt injection and social-engineering detection within customer chats, beneficiary risk checks before payouts.
Micro-example
For a small-ticket loan, the agent completes KYC, pulls bank statements, extracts features (cashflow vol, salary regularity), queries the risk engine, and issues a conditional approval—all in minutes, not days.
Implementation Guide for FinTechs
Before you dive in: This implementation guide bridges the gap from idea to production. It helps you pick the right first use case, design the right guardrails (approvals, audits, PII), and choose an architecture that blends agents and rules, so you cut TAT without adding risk.
What you’ll walk away with: a clear rollout plan (canary → pilot → scale), ownership model across product/risk/IT, measurable KPIs (TAT, success rate, exception rate, SLA), and a checklist to prepare your stack (APIs, permissions, environments, logging). With that context, the next section details the technical requirements.
Technical Requirements
Architecture building blocks: Think in layers: an agent runtime that plans/acts, a secure tool layer that connects to your core systems (CBS, LOS/LMS, KYC, payments), and a state layer (memory + event bus) that coordinates multi-hop work and retries. Wrap this core with guardrails (rules, approvals, RBAC, and data boundaries) and observability (metrics, traces, and audit logs) so that every action is explainable and compliant. With these blocks in place, you can plug in new use cases without rebuilding the foundation.
- Orchestrator / Agent runtime: the “brain” that plans steps, chooses tools, and reasons about outcomes.
- Tool layer (APIs): KYC/KYB, payments initiation, virtual accounts, mandates (UPI Autopay/eNACH), payouts, ledgers, reconciliation, CRM, ticketing.
- Data & retrieval: structured stores + a retrieval system for policies, SOPs, product docs; redact PII before retrieval where needed.
- Guardrails & policy engine: define what the agent can do, when to escalate, and which actions require explicit consent.
- Observability: central logs, traces, and replay for audits; prompt/version registries.
- Security: vault for secrets, role-based access controls (RBAC), encryption at rest and in transit, and least-privilege service accounts.
API surface you’ll likely need: Start with read/write APIs into core systems – CBS, LOS/LMS, CRM, KYC/KYB, payments, so agents can fetch context and take actions safely. Add event/webhook subscriptions, idempotency + retry semantics, and scoped auth/RBAC for least-privilege access. Round it out with audit/approval/consent endpoints and a realistic sandbox to test end-to-end flows.
- Verification: KYC, CKYC lookups, DigiLocker fetch, PAN/GST checks
- Payments: UPI collections, UPI Autopay, eNACH mandates, virtual accounts
- Payouts & ledgers
- Risk: fraud scoring, velocity checks, device fingerprint
- Ops: ticketing, notifications (email/SMS/WhatsApp), CRM
With Decentro, many of these are available as ready-to-use modules—so your agent has reliable “hands” to act with.
Integration Strategy
- Pick a narrow, high-leverage wedge
Examples: generate foreclosure letters, resend statements, mandate status checks, address updates, and dispute intake. - Parallel run with humans in the loop
Shadow mode first (agent produces suggestions; humans approve), then move to supervised autonomy with clear kill-switches. - Instrument everything
Track first-contact resolution (FCR), handle time, abandonment, escalations, CSAT, and error taxonomy. - Iterate by risk zone
Tier your use cases: green (automate), amber (supervised), red (human only). Promote/demote based on performance and policy.
Legacy compatibility: Connect agents to your current systems using small API wrappers or file/queue handoffs. Keep a safe fallback (basic UI automation) with timeouts and a kill switch. Roll out gradually, starting with a small % of cases first, check results, then scale. This way retries won’t create duplicates.
- Wrap older systems with thin APIs or RPA bridges (a temporal solution).
- Use event-driven patterns (webhooks, queues) where possible to decouple the agent from synchronous bottlenecks.
- Maintain idempotency, especially for payments, mandates, and payouts.
Compliance Considerations
Run policy checks and get approvals before any update or money movement. Protect data by default, use least-privilege access, capture consent, encrypt sensitive fields, and set clear retention rules. Stay audit-ready with time-stamped logs, tracked rule/model changes, and one-click, regulator-ready exports.
- Verifiable logs: store prompts, tool calls, responses, decisions, and final outcomes with timestamps and hashed IDs.
- Consent & purpose limitation: capture customer consent when accessing personal data or taking actions on their behalf.
- Data minimisation & localisation: pull only what’s needed; keep PII where policy requires; anonymise in analytics.
- Standards: align with your obligations (e.g., PCI DSS for card data), and internal infosec policies.
- Vendor risk: assess model providers, API partners, and data processors. Keep a clear inventory of where data flows.
Team & Skills
Core squad: A small pod that owns the first agent use case end-to-end: PM, an engineer for agents/integrations, and a risk/compliance owner (with DevOps help as needed). Their job: set guardrails, ship a safe MVP fast, track TAT/quality, and scale from Day 0 → pilot → production.
- Product owner for agent use cases and risk tiers.
- Backend engineer(s) to integrate APIs and build the tool layer.
- ML/LLM engineer for prompts, retrieval, evaluation harness, and guardrails.
- Risk & compliance partner to encode policies into the agent.
- Conversation designer (yes, still valuable) to shape tone, disambiguation, and fallback paths.
- SRE/Platform for reliability, cost, and security.
- QA analyst with scripts that test both deterministic flows and “fuzzy” language paths.
Benefits & ROI
- Operational efficiency. Agents handle the busywork, answering common questions, updating details, checking mandates, and simple reconciliations, so your teams spend time on higher-value tasks. They work 24/7, smooth out peak loads (festivals, salary days), and cut repeat handoffs between back-office teams.
- Customer experience. Faster answers, fewer hops, and a consistent tone – plus proactive nudges before issues snowball. Add multilingual support and clear explanations to make complex policies easy to grasp.
- Competitive advantage. Quicker “time-to-yes” in lending, earlier fraud/risk flags, and a digital brand that feels effortless, customers notice when things “just get done.”
Challenges & Solutions
| Challenge | What actually happens | Practical mitigation |
| Hallucinations / wrong actions | Agent “sounds” confident but is wrong; takes an unsafe step | Restrict actions via policy engine; require multi-factor confirmation for risky steps; add post-condition checks after every tool call |
| Latency | Users drop off if answers take > 5–8 seconds | Cache frequent answers; pre-compute; use streaming responses; parallelize tool calls where safe |
| Data leakage | Sensitive data leaves safe boundaries | PII redaction; on-prem or VPC endpoints where required; encrypt everything; strict RBAC |
| Prompt injection/jailbreaks | Malicious instructions trick the agent | Input sanitisation; allow-listed tools; content and system guardrails; regular red-teaming |
| Policy drift | Agent behaviour diverges from compliance updates | Treat policies as code; version them; add policy tests to CI |
| Integration fragility | Upstream APIs change, flows break | Strong contracts, retries, circuit breakers, idempotency keys; observability with alerts |
| Over-automation | CX dips when nuanced cases are forced through bots | Clear escape hatches to humans; route by intent/complexity/impact |
| Change management | Teams distrust the agent | Roll out with “assist” mode; publish weekly scorecards; reward agent-identified savings and CX wins. |
Future Outlook & Getting Started
Market trends to watch
- Teams of specialist agents: Small agents for KYC, collections, disputes, etc., hand work to each other to finish jobs faster.
- Agents + rules together: Use rules for must-not-fail steps; let agents handle messy, changing tasks around them.
- Proactive by design: Agents watch ledgers, mandates, and risk signals and act early—not after a problem hits.
- Explainable actions: Every automated step comes with a plain-English reason and an audit log.
- Closer to your data: Run agents on-device or inside your VPC for better privacy and lower latency.
A pragmatic 90-day plan
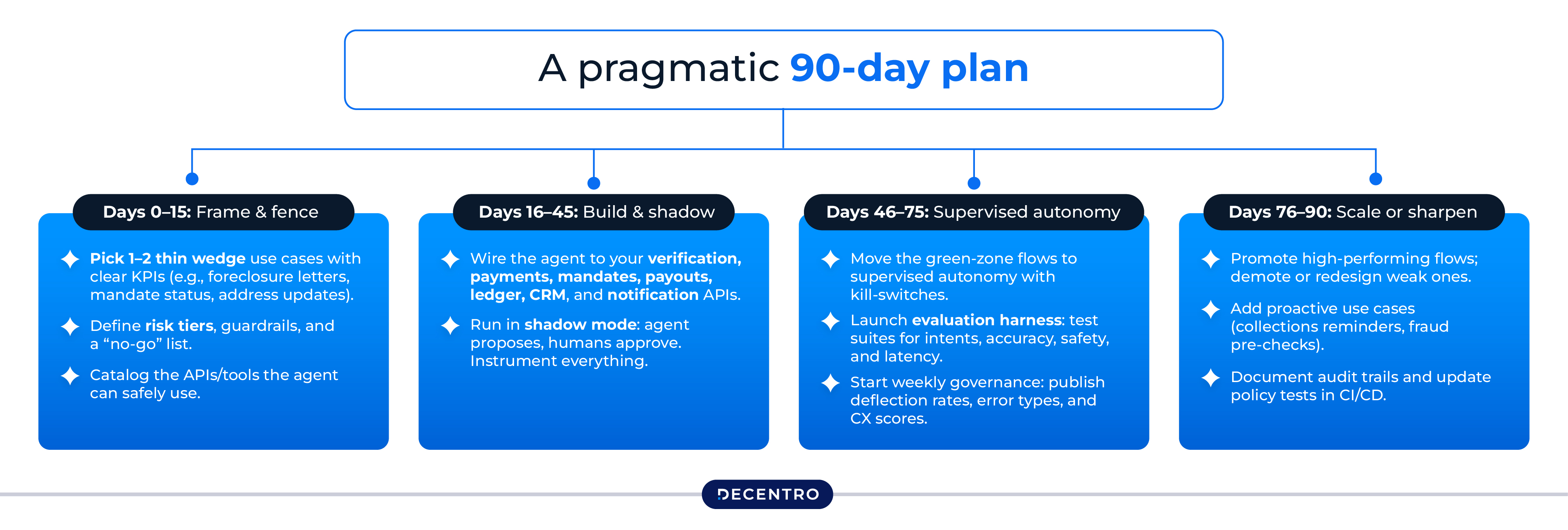
Days 0–15: Frame & fence
- Pick 1–2 thin wedge use cases with clear KPIs (e.g., foreclosure letters, mandate status, address updates).
- Define risk tiers, guardrails, and a “no-go” list.
- Catalogue the APIs/tools the agent can safely use.
Days 16–45: Build & shadow
- Wire the agent to your verification, payments, mandates, payouts, ledger, CRM, and notification APIs.
- Run in shadow mode: agent proposes, humans approve. Instrument everything.
Days 46–75: Supervised autonomy
- Move the green-zone flows to supervised autonomy with kill switches.
- Launch evaluation harness: test suites for intents, accuracy, safety, and latency.
- Start weekly governance: publish deflection rates, error types, and CX scores.
Days 76–90: Scale or sharpen
- Promote high-performing flows; demote or redesign weak ones.
- Add proactive use cases (collections reminders, fraud pre-checks).
- Document audit trails and update policy tests in CI/CD.
Build Agentic Finance on Proven Rails
Great agents need great hands. Decentro gives your AI agents reliable rails to verify identities, collect payments, set up mandates (UPI AutoPay/eNACH), manage virtual accounts, trigger payouts, and keep ledgers clean—backed by audit trails, high uptime, and security your risk & compliance teams expect. If you’re exploring AI agents in finance and want to move fast without breaking things, we’ll help you pick the first wedge, map the APIs to power it, and design a safe, phased rollout with measurable ROI. Talk to us.
Summing up (quick reference):
- AI agents = goal-driven systems that reason, use tools (APIs), and complete tasks end-to-end.
- Start with reactive (assistive) support, then move toward autonomy where policy allows.
- Focus on multi-step flows with verifiable outcomes.
- Instrument everything: FCR, AHT, CSAT, error categories, escalations.
- Build with guardrails: policy engine, allow-listed tools, consent/approvals.
- Pair agents with a reliable API infrastructure (like Decentro) to execute safely.
Frequently Asked Questions
What are AI agents in financial services?
They’re goal-driven software “doers” that plan steps, call your systems (CBS, LOS/LMS, KYC, payments, CRM), and finish tasks end-to-end with guardrails and audit logs, so work gets done faster and with fewer handoffs.
How much do AI agents cost for banks?
Costs depend on scope, but think in two parts: (1) setup/build (one-time: workflow design, integrations, policy reviews) and (2) run-costs (LLM/API usage, infra, monitoring). For simple service requests, teams often model ₹5–₹15 per automated interaction (illustrative), with costs rising with complexity (e.g., KYC, payouts, reconciliations). A quick pilot is the best way to validate your own numbers.
What’s the difference between AI agents and chatbots in banking?
Chatbots mostly answer questions; agents complete actions. Agents keep context, call APIs, follow rules/approvals, and log every step, so you measure outcomes like TAT and success rate, not just CSAT or deflection.
How long does it take to implement AI agents in financial services?
If your APIs and rules are ready, a focused pilot can be shipped in 3–6 weeks; production hardening and scaling usually follow over 8–12 weeks. No/limited APIs, data silos, or complex approvals add time; clear workflows, test data, and a small cross-functional squad speed things up.